Extending Cyber Security to the Connected Edge
The development of the smartphone started a trend of connected devices that not only perform some form of computing and decision making, but that has changed how we relate with the world around us. These devices are connected through networks and cloud services that provide easy access and sharing of information. In order to solve for market demand, there is a rapidly multiplying number of connected devices designed to transform and innovate how we seamlessly interface with the world. This trend is changing how we relate to the automobile and factory, but it is also creating cyber security challenges that industry integrators will face. In these markets, there is a much higher demand to operate reliably, which presents unique cyber security challenges when extending the connected edge.
For instance, the automobile is no longer simply a tool used to get us from point A to point B. It is becoming a platform that provides us new means to interact with the world and improve our quality of life. This is being achieved through connectivity and the sharing of data, such as how to optimize battery performance or updating navigation with changing landscapes. The automobile platform is becoming a way to connect and integrate services in a fashion that mimics the development of the smartphone in an environment that demands near absolute safety, integrity, and accessibility.
The industrial market is undergoing significant changes as new technology advances serve as a catalyst for higher productivity. The demand for increased productivity is changing how we interoperate and interact with the factory. The need to interface with the factory in a more intuitive and seamless manner is driving the next industrial revolution. With the wave of advances defining Industry 4.0, there is increased connectivity and requirements for access in the factory. The devices at the edge need to be more capable, moving the analytics further to the edge and increasing functionality, autonomy, and connectivity. The data links between the devices in the factory and the traditional field connection point have to adapt to be more capable; providing increased visibility and control from the cloud. In an industry known for focusing on stability and availability, there is increasing demand for flexibility.
Solving for the demand to interface with the world around us in a more seamless and intuitive manner drives new capabilities and technologies. However, a major byproduct of these developments is the need for security. Cyber security is a principal factor in market segments that demand high reliability and safety. Those who have malicious intent, commonly called bad actors, can exist within or outside an organizational system and can have many different motivations. The threat to connected devices exists both through the network as well as physical access. Cyber security applied to these edge devices need to adequately address the threat.

Analog Devices provides solutions that connect the physical world to the digital world, here analog-to-digital conversion takes place. ADI is uniquely positioned in the market to push cyber security further to the edge, where data is established. Establishing trust in the data further down the signal chain provides users with more confidence in the decisions they are making from the data because they have a higher expectation that the data is accurate. Cyber security is a key element of ADI’s strategy not only because it is necessary in our markets, but because it is a catalyst for enabling our customers’ systems and increasing the value of the information from our sensors. Ultimately, what our customers care about is trusted data. This means establishing that the measurement is accurate and there is integrity in the data.
Why Cyber Security Is Hard to Understand
Cyber security is not always easy to understand because it is a constantly changing, complex problem and it is a factor at every point in a system or device life cycle. Security is a system solution and the system is only as strong as its weakest link. There is a significant number of cyberattacks today, with successful attacks increasing as systems become more complex.

System vulnerabilities can be demonstrated though many examples of weak links. In 2016, automotive key fobs were compromised for an entire fleet because only four root keys were used for the past 20 years. In 2011, high assurance identity tokens were exploited through exposure of manufacturing artifacts created and stored on the factory floor. In 2017, a vehicle was accessed through the cellular link, which allowed hackers the ability to update the operating system and rewrite the program remotely. The Heartbleed Open SSL buffer over-read vulnerability left 200,000 active servers and devices vulnerable and without the means to receive security updates today. To further elaborate on why cyber security can be hard to understand, security is never done. As new vulnerabilities are discovered and new methods of hacking devices are established, devices and systems must constantly be updated to adjust to security changes.
The constantly changing, complex environment of cyber security makes it difficult to understand the problem. The interplay of systems and devices presents a complex security problem that is not solved by any one solution. The solution requires a secure system architecture with an in-depth defense approach. Past methods, such as air gapped systems, do not provide adequate protection in today’s connected world and with the availability of physical access to devices on the network. The problem needs to be addressed as early as possible in the design cycle to allow for a security by design approach, and an architecture and life cycle design that accounts for ever changing and growing threats.
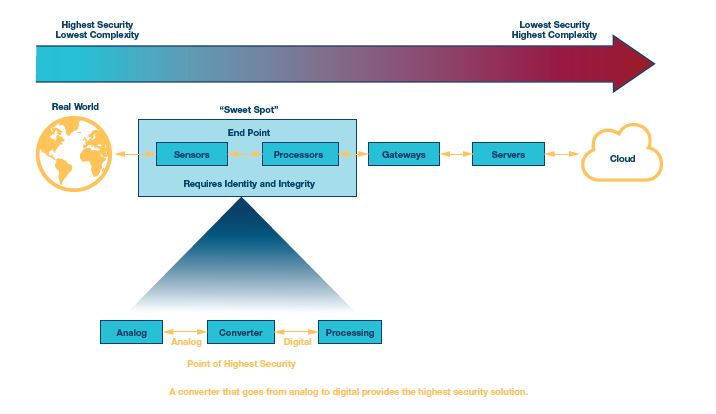
Why Implement Cyber Security at the Edge
Cyber security has traditionally been perceived as an IT problem, requiring implementation of good network protocols, operating system and application protocols, firewalls, malware protection, and other solutions designed to guard against network attacks. However, there is not always unilateral agreement on what constitutes the edge. For network providers, the edge is often considered as the router, gateway, PC, tablet, or other high functioning device. In the industrial automation space, it may be the actuator that controls a pump. In today’s changing environment, these edge devices are adapting to include more functionality and higher levels of connectivity. With these changes, the risk assessment of the system changes. Where cyber security might not have been needed previously, these devices may become the weakest link in a system if proper measures aren’t taken to guard against the risks.
Implementing cyber security at the edge gives users more confidence in the data. To reach the highest levels of security, security has to be applied much earlier in the signal chain. Providing confidence that the data has not been manipulated by validating the source provides a higher level of confidence in the decisions being made from that data. ADI is in a unique position to redefine the secure edge by leveraging existing solutions that connect the physical world to the digital world.
When it comes to cyber security, complexity is the enemy. For every 1000 lines of code, there are two to three coding errors, which provide avenues to maliciously exploit a system. Implementing cyber security at the point of lowest complexity provides an environment that gives higher assurance that security has been implemented correctly. Secure operations can take place within security boundaries implemented within the edge devices, pushing the chain of trust closer to the real world. In highly complex networks, organizations and individuals must continually update applications and configurations to protect against the latest threats. At the device level, one can limit the secure operations to a footprint that becomes much more manageable throughout the life cycle of the product.
Implementing cyber security where the physical world meets the digital world provides the highest level of security by establishing trusted data earlier in the signal chain. As IT and OT converge, cyber security will not simply be an IT network problem. Devices that have not traditionally been security hardened will need to provide a root of trust in the data and security features will need to be applied based on the risk assessment and constraints of the system. Substantiating identity and integrity at the edge establishes trust in the data earlier, providing more confidence that the data is accurate. ADI is able to provide unique value by redefining the secure edge and applying a hardware root of trust in the data.
Cyber Security Strategy to Address the Market
Analog Devices is a leader in precision sensing and has a large market share in devices that are relied upon to make real-time decisions in high reliability markets. As our customers adapt to the industry’s megatrends and seek to meet the demands that change how we interact with the real world, Analog Devices is in an instrumental position to provide the highest level of confidence to our customers. In addition to providing technologies that push capabilities ahead of what is possible, we are making strides to address the problems created as byproducts of these advancements and cyber security is at the forefront of our priorities.
As we evaluate our traditional markets, there are distinct differences in how these markets perceive cyber security and their level of maturity for adopting security solutions. Analog Devices has a strong product portfolio of secure crypto solutions targeted for the defense and government market. This cyber security expertise has been obtained through the acquisition of Sypris Electronics. By leveraging this strong base in nation state-level cryptographic solutions, we are pivoting into adjacent markets that must operate with high reliability and are driving cyber security solutions further to the edge, where Analog Devices traditionally plays in precision sensing.
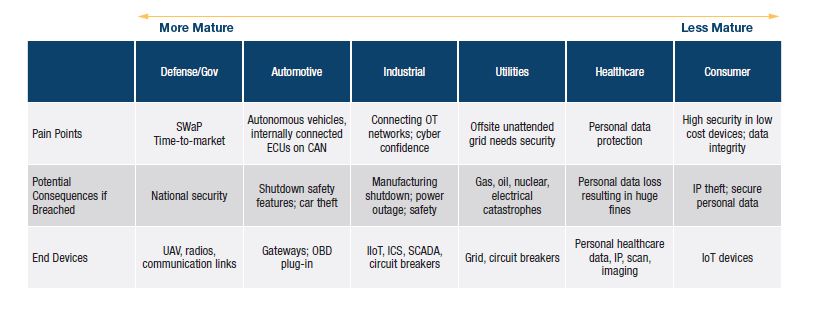
Cyber security applies to all markets and Analog Devices’ strategy is to effectively assess demands from each market and apply the right cyber security solutions to enable a secure device architecture congruent to the risk assessment within each application. Understandably, cyber security demands are more arduous in markets that must operate with high reliability and subsequently have a more advanced cyber security posture. Our primary focus is to address the industrial market and develop solutions that accelerate the adoption of Industry 4.0.
The industrial sector has similarly seen numerous attacks that range in severity. Some of the most significant have been nation state attacks on key infrastructure targets and targets that could result in loss of life. These attacks have been initiated through malware injected into systems, typically through physical access of a control unit or PLC connected to the factory network. With the emergence of Industry 4.0, the point of attack will continue to expand further to the edge as traditional I/O devices start having more control over operations and are connected through Ethernet to the PLC or directly to a cloud.
With this ever expanding functionality and higher functioning connectivity on a network, the edge devices that at one point had little opportunity to do system damage become a much higher risk to the system. Due to the sophistication of attacks in this market space, the ability to implement cyber security techniques correctly becomes paramount to the overall system vulnerability. This implementation requires an accurate threat assessment to understand potential points of attack and layering on security solutions to adequately protect against these threat vectors. For an at the edge device, establishing appropriate security boundaries and enabling a hardware root of trust greatly increases the system security posture.








