DDoS attacks are growing in complexity and volume and represent a major threat to any organization. Service providers and enterprises require expertise and knowledge to successfully deal with these threats. While large organizations have the budget to develop in-house expertise to address DDoS Attack, there are still administrative burdens associated with protecting computing and infrastructure resources.
Traditional DDoS protection solutions use rate limiting and manual signatures to mitigate attacks. Rate limiting can be effective in mitigating DDoS attack but can result in a high rate of false positives. Manual signatures are used to pinpoint the offending traffic in order to reduce the number of false positives. However, manual signature generation process can take hours or even days. This increases time to mitigation and can render the protection strategy ineffective.
Effective DDoS protection combines machine-learning algorithms with negative and positive protection models, as well as rate limiting. The combination of these techniques ensures zero time to mitigation and requires little human intervention.
Machine-Learning Algorithms for Detection and Mitigation
The most effective way to protect against a DDoS attack is to be able to automatically and accurately identify the attack traffic and drop it. Machine-learning plays a key role in effective DDoS mitigation strategies.
Machine-learning algorithms for attack mitigation employ various learning, detection, characterization and mitigation schemes:
- Creating a profile of normal or legitimate traffic, and detecting anomalies or deviations from the normal traffic behaviour.
- Characterizing the attacking traffic and creating an initial signature.
- Automatic optimization of the initial signature with closed-feedback mechanisms. In many cases, the initial signature is subject to false-positives, and further optimization takes place while measuring the effectiveness of the signature along the process.
- Identifying the end of attack to stop mitigation.
When attacks are fully randomized, positive protection models employs a signature generation logic that drops all traffic aside to legitimate traffic learn during peacetime.
Zero Time to Mitigation
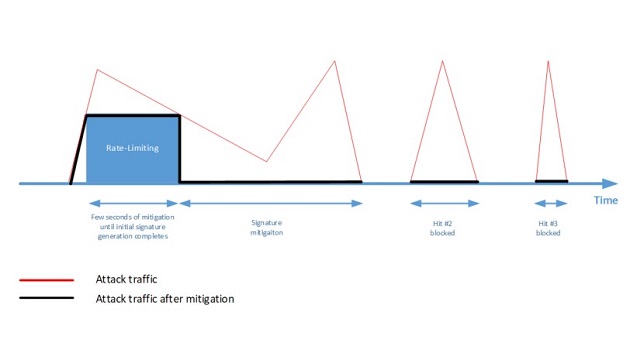
While negative and positive machine-learning algorithms are best at mitigating attacks with minimal false-positives, the process of automated signature generation can last for a few seconds. Sophisticated attackers may use this short window, where no signature is in place, to unleash a high-volume, short-lived burst attack at the target. This attack can last only few seconds and can bring down a service if no protection is in place. This is where rate-limiting is very effective. It limits the attack traffic to a rate that the protected services can sustain, and fill the mitigation gap of few seconds until the signature is ready.
Rate-limiting starts attack mitigation immediately in order to provide zero time to mitigation and is only used for this first occurrence. Once a signature is ready, it is automatically applied to mitigate reoccurring attack hits while eliminating false positives. This ensures continued zero time to mitigation across the entire attack campaign.