Courtesy Nuvoton
Security in IoT has been widely discussed. Although the security issues seem to be very large and complex, it still has some guidance and method that could be referred which is based on experience. More and more frameworks and certifications have developed into a sound management mechanism based on them.
The author believes that to achieve a complete IoT security consideration is from the end-to-end system problems. From this point of view, the IoT security problem can be slightly converged into “improving the security considerations of new network nodes”. This article will start from the IoT node side, analyzing and discussing the microcontroller (MCU) chip architecture design of the endpoint device side in the IoT environment.
Basic Security
In general, secure transmission is designed to meet three requirements: Confidentiality, Integrity, and Authenticity. The meaning of the requirements is explained in the following table:
| Confidentiality | Integrity | Authenticity |
| To ensure that during the information transmission process, the original content will not be leaked to third-party individuals or organizations that should not be received | To ensure that after the information is delivered to the target receiver, it can still be restored to the original data content of the sender | To ensure that both parties of the information transfer mutually recognize each other, and each transmission is individually identified |
Table 1:Security Requirements for Information Transmission Main Item Description
The three security requirements must be met simultaneously, and the absence of any one of them will create security problems. Over the years, many of the security technology development purposes have been to promote the achievement of the above goals, some of which have matured and some of which continue to evolve.
“Cryptography Algorithms” is the security cornerstone of modern information communication and communication technology, and the encryption/ decryption functions developed on its basis play an important role in the field of information.
“Encryption” and “decryption” function is an important component of building “privacy” such as: symmetric encryption and decryption of AES, DES/3DES, asymmetric RSA, ECC and other algorithms. The application of these technologies derived from the information in the transmission process is not easily or unchanged to be intercepted and interpreted.
The Hashing function is to achieve the “integrity” of information such as SHA, MDx and other hash functions, which can ensure that any changes to the data can be recognized;Because when the data changes, that is, the type of data is not the original data, the check code calculated according to the original data will be different. The achievement of “Authentication” is achieved by combining the asymmetric algorithm and the hash function. A public key infrastructure (PKI) is a security infrastructure base on this concept.
So far, we have roughly explained the basic practice of achieving information and communication security based on cryptography, but with the development of the industry, the industrial security standards built on these foundations have gradually emerged such as secure http connections (https)、secure payment transactions (EMV based standards)、secure over-the-air software upgrade. Each industry sets standards that meet the requirements of individual industries to promote the safe development of individual industries.
Platform Security
After the above introduction, we can understand that the development of the existing IoT industries has attached great importance to the security issue of information and communication; Therefore, I believe that the focus of IoT security is likely to fall on more and more connected devices. When these devices are widely set up, they will not require too many human operations, and their security requirements, including information and communication, functional operation, etc. will face new challenges.
Imagine the household meter including electricity, water, and gas, which are remotely managed by networking devices. If the control could be access easily by the hacker, the energy supplies would be cut off or causing personal safety. For these reasons, when discussing IoT security-related issues, we must start with system architecture, including security architecture or security platform.
This article focuses on MCU security platforms, which cover a wide range of issue. For example: 1. The protection capabilities of the MCU itself. 2. The closure of the MCU internal memory. 3. The privacy of key storage and effective practices against electromagnetic analysis to steal information. 4. Even more important software protection for intelligent handheld devices need to be considered. Therefore, according to the system characteristics of the IoT, we can classify the above MCU security risk issues into the following three aspects:
- Networked or not to launch a security attack: The hacker should touch the device or just through the network when launching an attack.
- The cost of launching a security attack: The target of the attack was a Notebook with Wi-Fi or a sophisticated device in the lab.
- The result of an attack: It only affects a single node device or the entire network.
When we want to design a secure IoT node device, the above three aspects can help us evaluate the resources invested and the level of security required.
Threat and Attack
From the above explanation, we can understand that when the MCU is in the design stage, the consideration of information security protection is based on the end product requirements. According to the different application needs to develop suitable security protection requirements standards. In today’s commercial market, card applications in the financial industry have the highest level of chip security protection.
The security protection requirements for the chips on traditional networking devices like mobile phones, desktop computers, laptops and tablets, and other Internet devices depend on the user’s operating environment, the complexity of the operating system, and the performance of the processor. Therefore, it mainly relies on software-level technology to achieve security protection requirements. By defining the emerging IoT chip security requirements between the above two, we can analyze the actual security protection requirements covered.
Based on the OWASP (Open Web Application Security Project) organization, the top ten items of the IoT that are most likely to cause security problems are:
- Insecure Web Interface
- Insufficient Authentication/Authorization
- Insecure Network Services
- Lack of Transport Encryption
- Privacy Concerns
- Insecure Cloud Interface
- Insecure Mobile Interface
- Insufficient Security Configurability
- Insecure Software/Firmware
- Poor Physical Security
We can find that the above items still focus on the topic of IoT security networking, mainly because most of the Internet of Things devices, especially the terminal nodes, are equipped with simple resources to carry out simple sensing and data transmission work. With the rise of cloud computing and big data, key data storage and computing will return to the cloud, so we need to carefully consider the degree of security protection requirements of end nodes is a topic when building IoT system.
Chip Architecture
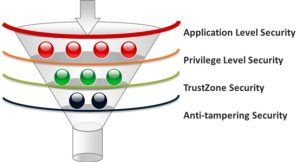
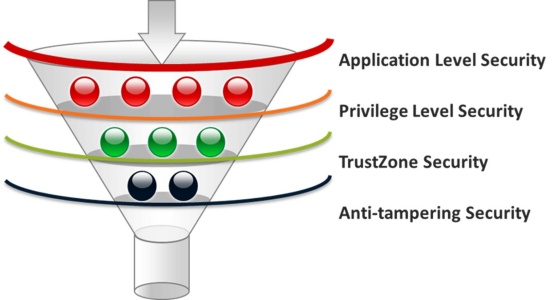
The CPU cores based on the ARMv8.x-M architecture with the integration of TrustZone® technology, which used to be available only in the Cortex-A series. This technology is more capable of building a deeper secure computing architecture than current general-purpose MCUs. We investigate Arm’s Cortex Series CPUs and categorize the different security levels for Embedded System as follows.
| Security Feature Level | The Existing Solution |
| Application Level Security | Most MCUs in the market |
| Privilege Level Security | Chip with MPU (Memory Protection Unit) or MMU (Memory Management Unit) |
| TrustZone Security | TrustZone for Cortex-A or
TrustZone for Cortex-M |
| Anti-tampering Security | Tamper-resistant for Physical Security |
Table 2:ARM Embedded System Security Requirement Table
- Application Level Security
When we look at the processors on the market today (CPU、MPU、MCU) , almost all processors can support this level of security requirements because it is essentially the security mechanism provided by the software. The application level security can be achieved as long as the system developer has a secure mechanism for both the local processor system and the remote/cloud system at the time of writing the program.
- Privilege Level Security
This level distinguishes system programs (such as the OS kernel) and applications into Privileged and unprivileged states when executed.
In this way, the processor has a different state when running the program, so that the memory management unit (MMU) or memory protection unit (MPU) attached to the processor can play a role to prevent the wrong program or malicious program from finding vulnerabilities in the system design. It is like opening a blacklist for the snap-in to prevent vandalized malicious programs. As long as the blacklist condition is met, the protection unit will issue a warning and even force the system to stop operation to avoid unnecessary trouble.
- TrustZone Security
This level targets software running on different processor regions. It uses to consider that programming will eventually take into account which processor region it will operate. The most common classifications are secure region and non-secure region. Compared to the previous level(B), it adds more protection to the system. It actually isolates the processor that the software interaction between the secure and the non-secure zone is strictly controlled. It’s like opening a whitelist that only if meeting the conditions can the software of the two districts interact, which is a more stringent system security rule. Although the practice does not necessarily have different processor regions of the entity, TrustZone can be seen as practicing the whitelist rules on system security design.
- Anit-tampering Security
This type of security chip is designed for a specific purpose, considering the MCU’s protection against physical attacks. Because the designer cannot control the use environment of the MCU product and the amount of confidential information to be protected (e.g. personal funds) is not large, physical protection is carried out. For example, MCU line layout design, pin signal undetectability, overall software speed adjustment to prevent comparison… etc.
Due to the consideration of multiple electronic attack prevention technologies, the MCU design should not be too complex to generate more vulnerabilities. Nevertheless, security protection technology is still necessary for IoT products, and there is still room for further discussion on how to take into account the diversified needs of realistic function design.
Design Thinking of Embedded Systems for IoT Security
Based on the above explanations, Nuvoton Proposed a “Funnel Security Design Thinking” that can be applied to the security design of IoT systems. Let designers think about the level of security their MCU systems need to provide. In addition to ensuring the safety quality of its design, it also achieves a more secure collaborative software development architecture in the MCU design field and take into account the flexibility of the networking device in the design diversity function through the application of ARM Cortext-M23 and Cortex-M33. We expect to see the advantages of ARM TrustZone for ARMv8-M used in more applications in the future. Combined with Nuvoton Security MCU, it can create a safe, convenient and widely used smart networked environment.