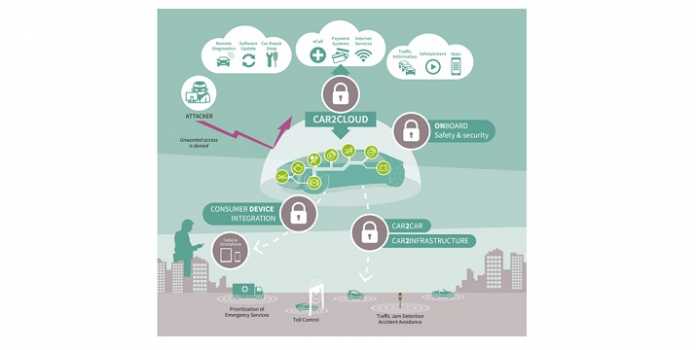
Infineon Technologies AG is enabling a crucial step toward greater cybersecurity in the connected car. The Munich-based company is the world’s first semiconductor manufacturer to put a Trusted Platform Module (TPM) specifically for automotive applications on the market. The new OPTIGA TPM 2.0 protects communication between the car manufacturer and the car which increasingly turns into a computer on wheels. A number of car manufacturers already designed in Infineon’s OPTIGA TPM.
The TPM is a hardware-based security solution that has proven its worth in IT security. By using it, car manufacturers can incorporate sensitive security keys for assigning access rights, authentication and data encryption in the car in a protected way. The TPM can also be updated so that the level of security can be kept up to date throughout the vehicle’s service life.
“As a computer on wheels, the connected car benefits from the experience of the IT industry,” said Martin Brunner, expert for automotive security at Infineon. “In the complex interplay between software, network and cloud, security hardware creates the solid foundation for secured communication. Backed by Infineon’s many years of expertise in the automotive and security areas, we have optimized the OPTIGA TPM for automotive applications. It is easy to integrate and substantially increases cybersecurity, from production to recycling of connected cars.”
Secured communication throughout the vehicle’s service life
Mobility of the future requires the exchange of huge volumes of data. Cars send real-time traffic information to the cloud or receive updates from the manufacturer “over the air”, for example to update software quickly and in a cost effective manner. The senders and recipients of that data, whether car makers or individual components in the car, require cryptographic security keys to authenticate themselves. These critical keys are particularly protected against logical and physical attacks in the OPTIGA TPM as if they were in a safe.
Whereas a vehicle has an average service life time of 12 to 15 years, security features and algorithms keep on being developed and enhanced on a continuous basis. The TPM’s firmware can be updated by remote access so the security it offers can be kept up-to-date, including the cryptographic mechanisms (cryptoagility).