What exactly is hardware encryption?
Hardware encryption is an approach to securing sensitive data by using a dedicated processor for calculating the encryption algorithms, dedicated memory for hosting the secure key, and isolation from the rest of the processing functions of the system for security and speed.
The dedicated processor hosts the mathematical functions used to execute the encryption algorithm. The dedicated memory is used to store the encryption key and is only accessible via the dedicated processor. By design, using a dedicated processor and dedicated memory results in isolation from the rest of the system, which reduces the potential attack surface and improves overall speed in performing the encryption functions.
Software encryption is an approach to securing sensitive data by using software tools to scramble or encrypt the data. The only way to unscramble or decrypt the data is with a password. Relative to hardware encryption, software encryption does not have a dedicated processor for executing the encryption algorithms, dedicated memory for hosting the secure key, nor isolation from the rest of the system processing functions.
Why do we need it?
The world is becoming “hyper-connected”.
Everyday more devices and systems, e.g., wireless devices, automobiles, factories, etc.,are connecting to communications links and the internet. Most of these devices are not designed to be secure against the vulnerabilities exposed by this new connectivity. Securing sensitive data is becoming a high priority as we reach hyper-connectivity of devices attached to the internet.This is especially true in market segments such as Energy and Industrial Automation, where high reliability and safety are a concern. Hardware enforced security provides a cost effective solution with enough security to protect against new attack vectors introduced by hyper-connectivity.Since bad actors (those who have malicious intent)can exist inside or outside an organization, security of connected devices must address threats from both network and physical access. Hardware enforced security can accomplish this when it is implemented correctly.
How is hardware encryption better than software encryption?
Hardware encryption is faster and more secure than software encryption.
Faster.Hardware encryption is critical for applications where time is of the essence. The speed at which hardware encryption engines perform computationally intensive calculations is a factor of 10 or 100 times faster than software encryption engines. What takes software 100ms to complete, may take hardware only 4ms. In addition, hardware encryption engines can perform its duties in parallel with system processes.
More Secure.Typical software encryption methods share processors and memory with non-secure operations opening up vulnerabilities for exploitation. This shared resource model increases the attack surface and allows adversaries to use software bugs in the system to inject their own code into the processor.This can compromise the device remotely over the network and ultimately expose the encryption key. Once the key is exposed, the system is completely compromised and no longer secure.
What are some of Analog Devices’ contributions towards this space?
Leading Edge Technology. One of Analog Devices’ newest products is SYPHER. It is a Field Programmable Gate Array (FPGA)-based cryptographic subsystem that removes schedule and cost risk by providing a turnkey hardware root of trust cryptographic subsystem and Trusted Execution Environment (TEE). This cryptographic subsystem contains all the needed security functions and protections allowing designers to focus on creating customer value while eliminating the burden of security design, certification complexities and vulnerabilities.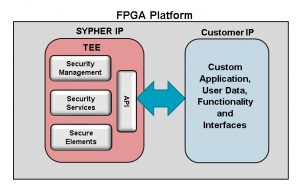
The subsystem isolates all the sensitive cryptographic operations and prevents any unauthorized access from the rest of the FPGA design while providing access to cryptographic functionality through a well-defined Application Programming Interface (API). Thus, SYPHER provides a proven security solution that allows a customer’s system to meet security requirements for both commercial and DOD environments without mastering all the complexities of secure design and the certification process. SYPHER follows the highest information assurance practices and can support both NIST FIPS 140-2 and NSA Type 1 certifications.
Customer Use Case. Analog Devices has used the SYPHER technology to add encryption functionality into existing Radio Frequency (RF) designs that already include an FPGA. Since FPGA designs enable upgrades to fielded products, Analog Devices is able to customize the SYPHER encryption modules to be inserted seamlessly into the RF product via a software upgrade.
Conclusion:
Analog Devices will continue to lead the development of technology solutions that fuel the “Internet of Things”, while making the incorporation of security at the edge easier for our customers, through turnkey solutions like SYPHER. Our innovative designs and technology solutions will continue to leverage hardware encryption methods to secure our customer’s most sensitive data in applications where safety and high reliability are vital, such as, the industrial automation, automotive, energy, and critical infrastructure markets.








