Imagine a scenario where we can anticipate crimes and stop it before it happens, ensuring a crime-free city. That’s the power of anticipation and prediction. In a popular American sci-fi movie ‘Minority Report’, there is a pre-crime unit – a specialized police department who apprehend criminals based on foreknowledge that they have acquired from the psychics called precogs. What’s interesting is that these precogs have visions that get displayed on the screen and they come to know – where, when and how a crime is going to get committed.
This is exactly what we need in the cybersecurity space – we need a precog. One that can help us anticipate cyberattacks. Talking about recent cyberattacks and major breaches there was one common thread, that of, missing information – either system error, misconfiguration, insider threat, vulnerability, or lack of visibility. To further validate this, the recent Data Breach Investigation Report of 2020 from Verizon confirms that in the last four to five years nothing has drastically changed when it comes to tactics and common methods adopted by hackers for data breaches. According to a research report by Ponemon Institute, the dwell time i.e. mean time to identify and contain the threat is still around 300 days.
If you look from a CISO’s perspective, their onus is to protect data in the present and future times, irrespective of where who or how it’s accessed. On one side they have the challenge of protecting the data, on the other side, they are haunted by the Cassandra syndrome, where the users are less aware of cybersecurity. There is also an executive board whose beliefs are closely tied to facts and figures, demanding evidence and ROI related to cybersecurity. Gartner talks about five board questions which the CISOs should be prepared to answer:
- Are we secure and compliant?
- Why is security so expensive?
- Why can’t security move faster?
- Why can’t we be a digital company?
- Why can’t we have a competitive edge from security?
If we can anticipate infrastructure or business technology change, we can tell the board that these are the areas of investment whether its people, process or technology that can help us mitigate the risk. Hence, security can become a part of this business technology fabric which can help us move faster.
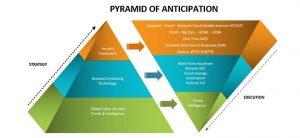
In order to achieve this, we have to look at building a framework which can help us anticipate better. Two key aspects should be considered while building this framework – strategy and corresponding execution.
- Building anticipation using global cybersecurity trends and intelligence, for instance, with the help of leading industry cybersecurity analyst reports, looking at past & present cybersecurity incidents or breaches with relevance to the respective industry and using threat prediction report by cybersecurity experts.
- Anticipate technological change adopted by organizations to stay ahead of the curve considering business demands (cloud adoption, IT-OT integration, Work from Anywhere which is the new norm).
- Organizations have started implementing tools and have adopted a framework which can provide more visibility across all the different security layers – endpoint, email, cloud, network or IIOT. Adopting XDR helps to anticipate and respond better across all security layers, which in turn improves the MTTD and MTTR.
PYRAMID OF ANTICIPATION
We have heard about Gartner’s Adaptive Security Architecture based on risk and trust. Apart from prevention, we also need to pay attention to other aspects – prediction, detection and response. We need to anticipate in order to respond effectively. The epitome of cybersecurity maturity comes with anticipation.
In this context, let’s understand how XDR can help anticipate better, providing:
- Realtime contextual visibility across multiple security layers: Endpoint, email, network, cloud, mobile and IIOT.
- Timeline and attack visualization: To know what, when and how.
- Correlation: Events, alerts across multiple technologies (for e.g. email and endpoint and network), also low and high severity events.
- Threat modelling framework: Mapping with MITRE framework for Tactics, Techniques, and Procedures (TTPs) to learn more about adversaries/threat actors.
- Automation and integration: Automation (prioritization of triggers or workbench) in the environment and integration with security exchange and threat intelligence platforms, to complement SIEM/SOAR and send high fidelity alerts and eliminate the noise.
- Threat intelligence: Proactive sweeping of IOC discovered in global cyber-attacks.
- Remediation/mitigation: Remediate and respond with confidence.
A recent report by ESG and commissioned by us, ‘The XDR Payoff: Better Security Posture, ESG Research, Sep 2020’, talks about the benefits of the organisations who have adopted XDR or organisations with XDR. It says that they are better protected and have suffered half as many successful attacks over the last 12 months. They can anticipate quickly – 2.2X more likely to detect a data breach/successful attack in a few days or less. They are also able to respond completely – 60% less likely to report that attack re-propagation has been an issue. When you have the bigger picture, you can understand the full impact and respond both faster and completely. There are fewer blind spots that allow for a resurgence of attacks.
(The commentary is Authored by Vijendra Katiyar, Director – Enterprise Business, India & SAARC, Trend Micro).