Introduction
Counterfeiting of products is a major global problem that goes beyond just the revenue loss for the manufacturers – it can result in the loss of the brand reputation due to poor quality of counterfeits. Traditionally, holograms have been used for ensuring the authenticity of the products. However, they can provide only limited information. A QR code is a more flexible tool, but it can easily be tampered, removed, or replaced. A much more versatile mechanism for product verification is NFC tag, which is electronic component that can store a small amount of information that can be read wirelessly over short distance. These tags contain a tiny NFC chip and a flexible antenna. NFC tags can be directly integrated into the product for example within the layers of fabric or inside the packaging of the product, thus making it difficult to tamper. Product information can be securely programmed wirelessly, after the final product is ready. To establish product authenticity in a retail store, the product information can be read using a dedicated verification terminal. This article describes in detail how the product verification using the NFC technology works in practice. It is an attempt to curtail nearly half a trillion dollars a year worth of global trade in fake goods [1].
NFC Technology
NFC is a wireless communication technology operating at 13.56 MHz that enables secure communication between two NFC-enabled devices over a short-range. NFC is a powerful technology which enables secure ad hoc communication between electronic devices without requiring ceremony like passwords and pins. NFC technology is extensively used for adding interactivity to inanimate objects thus making them smart. Ticketing, payments, and access control etc. are some of the primary areas where the NFC technology is widely deployed.
An NFC-enabled system has two parts – NFC Tag and NFC Reader. NFC Reader is the active component that initiates read & write operation on the NFC tag while also providing power to the NFC tag via electromagnetic induction. An NFC tag is generally passively powered device i.e., it receives its power from the NFC reader. The NFC Tag has an antenna coil which is used to communicate with the NFC reader and harvesting energy from the electromagnetic field of the NFC reader. The reader sends the data to the tag by modulating the RF field signal and the tag sends the data to the reader by modulating the load. When an NFC tag comes in the vicinity of the NFC reader, the NFC reader reads the tag attributes followed by an exchange of data. Each NFC tag is addressed uniquely using a unique identifier known as UID.
NFC employs different “technologies” and uses the same RF carrier, but each technology uses its own modulation scheme, bit-level coding, and frame format. There are mainly four types of NFC technologies (NFC-A, NFC-B, NFC-F, NFC-V). An NFC Tag may support one or more of the above-mentioned technologies.
The NFC tags are further classified into tag types depending on various memory, throughput, collision mechanism and ISO standards support.
Product verification at a retail store
In this section, we discuss the working of the verification system in detail. During the manufacturing of the product NFC tag is embedded in the product so that it is concealed and not removable by the user. If it is not possible to embed the tag into the product itself, the NFC tag can also be embedded inside the product packaging. Product details like serial number/model etc. are programmed into the tag using an NFC transceiver along with a product verification URL which points to a secure verification server.
The verification system uses a dedicated verification terminal installed in the retail store. When the product to be verified is taken near the NFC reader of the verification terminal, it reads the unique id of the NFC tag along with the stored product information and the verification URL. The terminal which is connected to the internet then sends a verification request to the cloud-based verification server to fetch the verification status and detailed product information. The verification results along with the product details like date of manufacture, dimensions, color, warranty details, etc. are shown on the display unit. The picture of the product is also shown on the display, which allows the user to physically verify the product description. If the internet connectivity is not available, the product data stored on the NFC tag is displayed on a NFC enabled Smartphone. This mechanism enables the buyer to readily check the genuineness of the product in the retail store and solve the problem of fake product sales in the market. A block diagram representation of the complete system is shown in Figure 1.
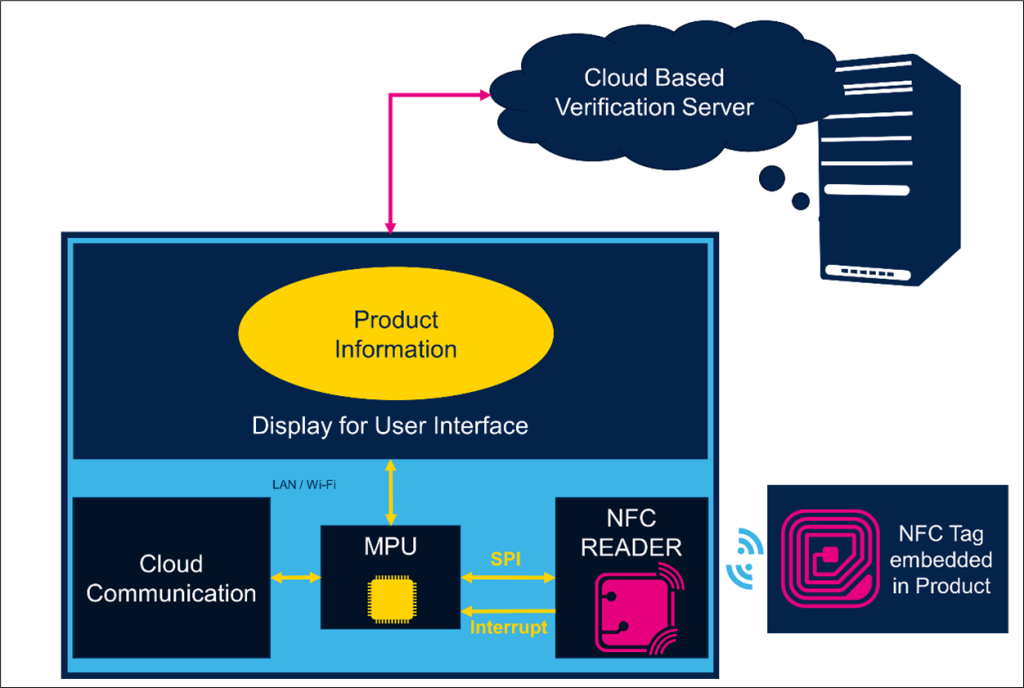
The solution can also be viewed as a customer engagement platform. Customers become more confident about product veracity if the terminal is provided as a self-service kiosk where customers can run the verification themselves. The system can also be used to display promotional information about the scanned product and also about the related products to help cross selling of the items. Whenever a product is verified on the terminal, the transaction is recorded by the verification server. This information can be used to run further analytics and uncover customer preferences about various products.
Software Architecture of NFC based Verification Terminal
This section describes the software architecture of the Linux-based verification terminal. Linux is the preferred host OS for this application because it’s proven, free and allows developers to leverage existing high-quality libraries.
The core functionality is provided by a “Verification Application” which communicates with the RFAL (Radio Frequency Abstraction Layer) driver to access data on the NFC tag. ‘RFAL Driver protocols’ is the set of functions that help the application to translate the communication with the NFC reader over SPI. ‘spidev’[4] is the driver module in the Linux kernel space which is responsible for handling all communication to and from the application over SPI bus. Figure 2 below, shows the overall software architecture of the verification terminal.
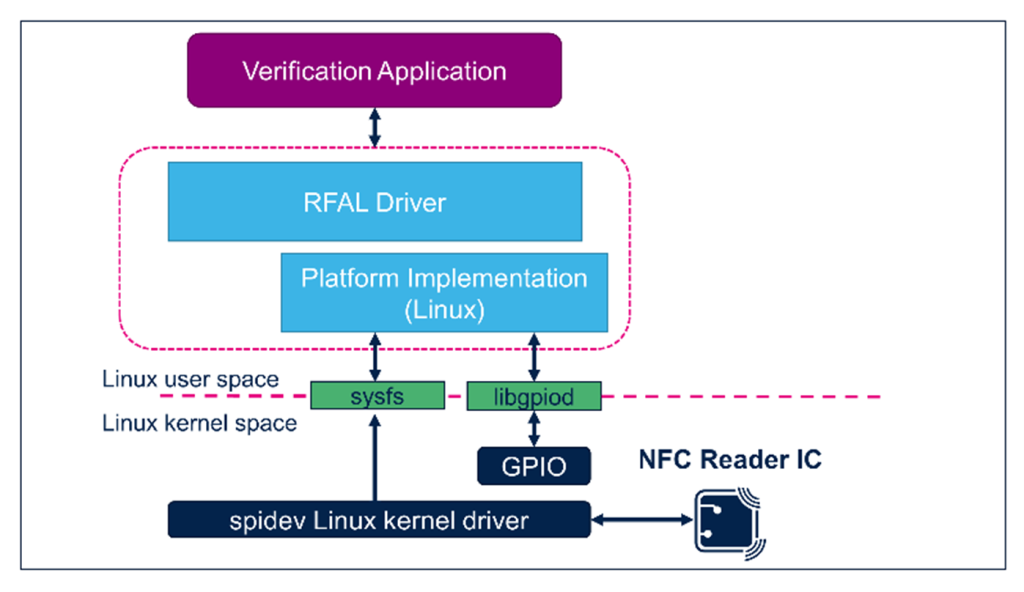
When an NFC tag is brought near the reader antenna, the NFC chip detects the presence of a new tag. An interrupt is triggered which is detected by the application software via libgpiod[5] mechanism of the Linux OS. The application software on the reception of interrupt starts communicating with the NFC chip to read the Unique Identifier (UID) and other data stored in the Tag. The solution makes use of excellent Linux networking libraries to communicate with the cloud and fetch the verification status as well as the product details. The results are shown on the display. Native UI Framework like GTK or Qt can be used to display the information in a rich GUI environment.
Hardware
The concept has been proven using a system solution built around the STMicroelectronics STM32MP1 discovery kit (STM32MP157F-DK2) which hosts a STM32MP1 series industrial microprocessor to allow users to easily develop applications using OpenSTLinux distribution software. The NFC functionality is provided by the NFC reader (ST25R3911B) expansion board (X-NUCLEO-NFC05A1) which docks on the connector available on the discovery kit (Figure 3) and various NFC tags based on the ST25DV04K NFC Type V tag IC. The implementation can be enhanced further by using NFC Reader (ST25R3916) based expansion board (X-NUCLEO-NFC06A1). ST25R3916 supports card emulation mode and is fully compliant with EMVCo 3.0. NFC front-end IC is interfaced with a microprocessor via suitable communication protocol for example SPI (Serial Peripheral Interface) or I2C (Inter-integrated circuits).

Conclusion
This article discusses the use of NFC technology for establishing the authenticity of consumer goods using NFC tag. Considering many reports of spurious medicines being sold during COVID-19 pandemic, such solutions can even help in saving lives. For high value products like gemstones or lifesaving drugs, the security of the solution can be further enhanced by using digital certificates stored in NFC tags. The solution can also be adapted to supply chains by employing blockchain to verify authenticity of the components at each stage in the supply chain thus ensuring that the final product is manufactured using genuine parts only. The solution can also be extended to include e-commerce scenarios, where the consumer can easily verify the product at home using a mobile application and an NFC-enabled Smartphone.
Authored Article by:
Subodh Vikram SHUKLA (Staff Engineer), STMicroelectronics
Prashant PANDEY ( Sr. Staff Engineer ), STMicroelectronics
Kumar Rahul TIWARI (Staff Engineer), STMicroelectronics
References:
[1] www.oecd.org








