With the rise of connected devices and the potential of exposure to large attack surfaces through various wireless technologies, there is now a great need to implement security by design in embedded connected products. Devices Connected to a digital network can be subject to an attack; iWave introduced a Security Suite to protect the billions of connected IoT devices.
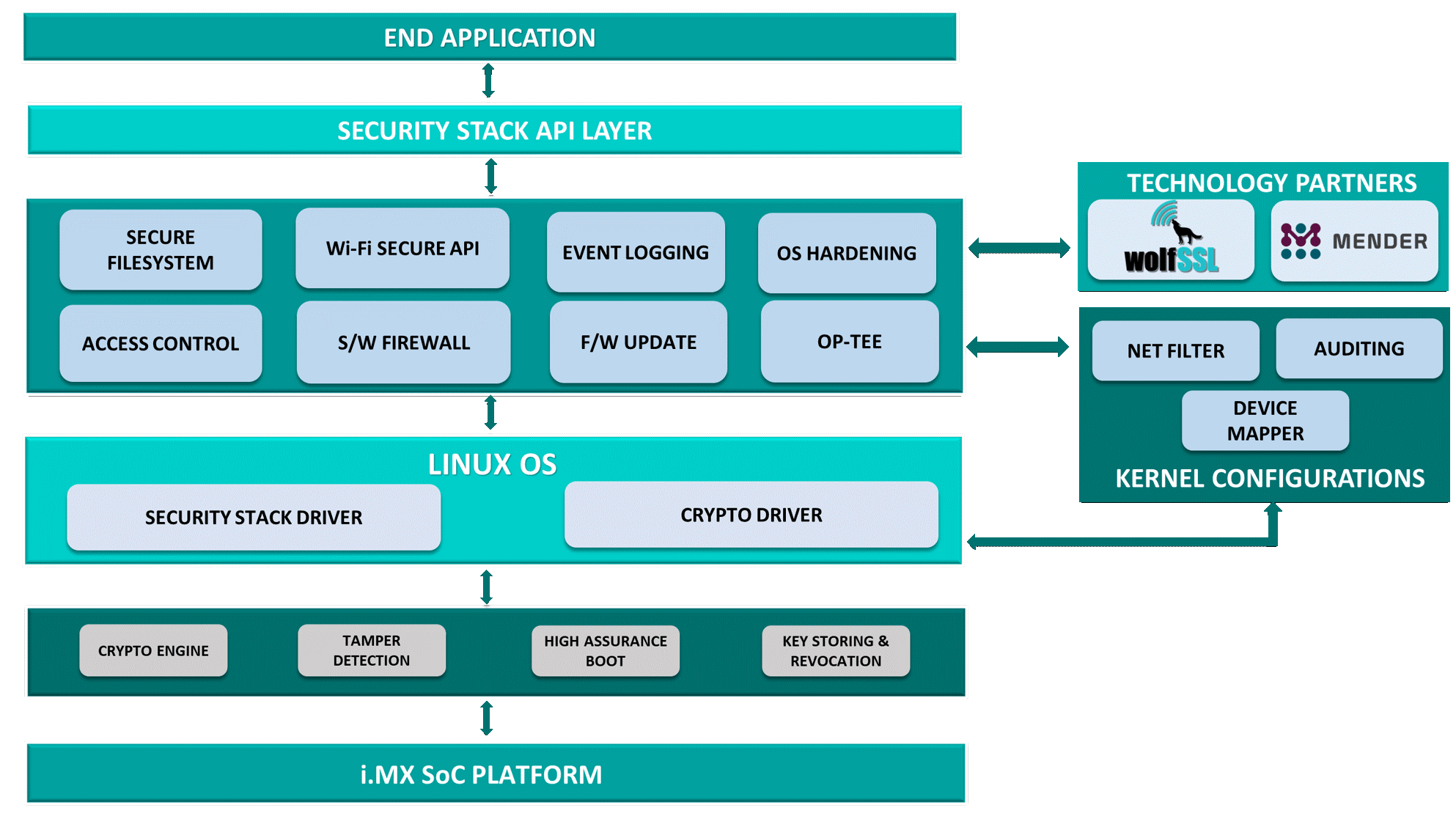
The iWave Security Suite is developed for NXP i.MX 6 series, i.MX 8, i.MX 8X and i.MX 8M application processors. With these processors built for numerous IoT and automotive applications such as gateways, multiple display applications, industrial systems, telematics units and V2X Solutions, there is a need to build a secure environment around the processors.
The iWave Security Suite helps secure connected devices, enabling them with security functions such as encryption, storage, data transmission and certificate management. The easy to integrate solution helps address the security challenges creating a safe and secure environment. The iWave Security Suite includes secure boot, Wi-Fi secure API, event logging, OS hardening, access control, software firewall and secure firmware update to name a few.
i.MX 8 and i.MX 8X family application processors feature Advanced High Assurance Boot (AHAB) and a Security Controller (SECO) while the i.MX 6 and i.MX 8M applications processors feature High Assurance Boot (HAB).
In i.MX 6, HABv4 enables ROM to authenticate the Bootloader and kernel image. In i.MX 8 and i.MX 8X family, AHAB enables SECO APIs to authenticate System Controller Unit (SCU) FW, SECO FW, Bootloader and kernel images which establish a chain of trust for the remaining software components by establishing a secure state of the system. The scripts provided by iWave along with the NXP Code Signing Tool (CST) makes the signing process extremely easy and simple.
Secure File System takes an end-to-end approach of protecting data by cryptography preventing unauthorized access to the data storage. Without proper encryption keys, data stored on an encrypted file system cannot be read (decrypted) with an entire secure storage partition encrypted and the root file system will be loaded.
Secure storage involves protecting data stored in storage devices like eMMC, MicroSD and many more. The Security Suite facilitates secure storage APIs to encrypt and decrypt the storage device partition on run time, data integrity and data encryption etc. Secure storage APIs use Cryptographic Accelerator and Assurance Module (CAAM) black keys to store the key in the CAAM blob format so that data/key is secured in a non-volatile storage device across power cycles.
The Security Suite supports robust easy to use APIs to integrate with 3rd party application and devices. The suite encompasses a compact package with a multi-level security solution.
More information on the Security Suite can be found here or watch this video for a quick overview :
For further information or enquiries, visit mktg@iwavesystems.com